As cyberattacks become more sophisticated, businesses must leverage advanced technologies to stay ahead of bad actors. Enter Artificial Intelligence (AI) – a powerful tool that has transformed how organizations detect, manage, and respond to cyber threats. By incorporating AI, cybersecurity teams can gain critical insights and automate time-consuming processes, allowing faster, more accurate decision-making.
What is AI in Cybersecurity?
AI in cybersecurity integrates artificial intelligence technologies, such as machine learning and neural networks, into security frameworks. These technologies enable cybersecurity systems to analyze vast amounts of data, recognize patterns, and adapt to new and evolving threats with minimal human intervention.
Unlike traditional cybersecurity tools, which rely on predefined rules to detect threats, AI-driven systems learn from experience, allowing them to predict, detect, and respond more effectively to known and unknown threats. By doing so, AI empowers organizations to enhance their cybersecurity posture and reduce the likelihood of breaches.
AI in cybersecurity involves technologies that can understand, learn, and act based on data. AI is evolving in three main stages:
- Assisted intelligence: Enhances what people and organizations already do today.
- Augmented intelligence: Enables new capabilities, allowing people to perform tasks they couldn’t do before.
- Autonomous intelligence: Future technology where machines will act independently, like self-driving cars.
Why is AI in Cybersecurity Important?
The importance of AI in cybersecurity cannot be overstated. As cybercriminals adopt more sophisticated methods, conventional security systems need help to keep pace. The sheer volume of data generated by modern networks further complicates the detection of threats, leaving many organizations vulnerable to attacks.
AI offers a solution to these challenges by:
- Enhancing the speed and accuracy of threat detection: AI can quickly sift through massive amounts of data to detect anomalies and identify potential risks, reducing the time it takes to respond to threats.
- Automating routine tasks: AI frees security teams to focus on more strategic efforts by automating time-consuming processes such as log analysis and vulnerability scanning.
- Predicting future attacks: AI can identify patterns in past attacks and anticipate new threats, helping organizations stay one step ahead of cybercriminals.
How is AI Used in Cybersecurity?
AI has numerous applications in cybersecurity, from detecting threats to automating responses. Below are three of the most common ways AI is leveraged:
Migrating from VM to EM for Smarter Risk Prioritization
Join this webinar to explore how Balbix’s AI-powered platform automates real-time risk management, enhances attack surface visibility, and enables smarter decision-making to reduce cybersecurity exposure.

Threat Detection
AI excels at identifying threats that would otherwise go unnoticed. Traditional security tools may overlook anomalies or struggle to recognize zero-day threats. However, AI-powered systems use pattern recognition and anomaly detection to spot unusual activity that could indicate an attack. Additionally, AI-powered systems can continuously scan networks and systems for vulnerabilities, automatically flagging potential weak points.
Threat Management
Once a threat is detected, AI is key in automating the management process. AI can prioritize vulnerabilities based on their potential impact, enabling organizations to address critical issues first and streamline patch management. This involves prioritizing threats based on risk levels and determining the most appropriate response. AI can help orchestrate responses in real time, minimizing the damage caused by an attack.
Threat Response
In addition to detecting and managing threats, AI can automate many aspects of threat response. This includes taking actions such as blocking malicious traffic, isolating affected systems, and generating incident reports. AI’s ability to adapt and evolve makes it a valuable tool for responding to emerging threats as they unfold.
Top Benefits of AI in Cybersecurity
1. Improved Threat Intelligence
AI enhances threat intelligence by analyzing large datasets in real time and providing predictive insights. This capability allows cybersecurity teams to anticipate attacks before they occur and take proactive measures to defend against them.
2. Faster Incident Response Times
Speed is crucial during a cyberattack, and AI enhances incident response by automating threat detection, analysis, and mitigation. Thus, the time from detection to action is reduced, and potential breach impacts are minimized. AI-powered systems provide improved context for prioritizing security alerts, enable rapid incident response, and identify root causes to mitigate vulnerabilities and prevent future issues.
4. Better Vulnerability Management
AI’s ability to identify vulnerabilities in networks and systems is another significant advantage. AI-powered vulnerability scanners can prioritize risks based on reachability, exploitability, and business criticality, helping organizations address the most pressing issues first. This reduces false positives and ensures that security teams are working efficiently.
5. More Accurate Breach Risk Predictions
Accounting for IT asset inventory, threat exposure, and security controls effectiveness, AI-based systems can predict how and where you are most likely to be breached so that you can plan for resource and tool allocation toward areas of weakness. Prescriptive insights derived from AI analysis can help you configure and enhance controls and processes to improve your organization’s cyber resilience most effectively.
6. Automated Recommendations
Another key to harnessing AI to augment human infosec teams is the explainability of recommendations and analysis. This is important in getting buy-in from stakeholders across the organization, understanding the impact of various infosec programs, and reporting relevant information to all stakeholders, including end users, security operations, CISO, auditors, CIO, CEO and board of directors.
Key AI Technologies in Cybersecurity
Machine Learning (ML)
Machine learning (ML) is a form of AI that enables systems to learn from data and improve without explicit programming. In cybersecurity, a typical application of ML is User and Entity Behavior Analytics (UEBA), which analyzes patterns and behaviors to detect threats.
For example, UEBA can flag unusual login activity by identifying anomalies in user behavior, such as abnormal login times or locations, which may signal a security breach and enable faster responses. ML excels in tasks like identifying network traffic anomalies and helping prevent attacks by recognizing irregular behavior before they escalate.
Deep Learning
Deep learning, a subset of ML, uses neural networks to analyze complex data and is highly effective in detecting advanced cybersecurity threats, such as evolving malware strains. In cybersecurity, Deep Learning is used to detect polymorphic malware, which constantly changes its code to evade traditional detection methods.
Deep learning models can analyze vast amounts of data and recognize underlying patterns in malware behavior, even when the code differs. For example, deep learning can identify anomalies in how files interact with a system, flagging malicious intent even if the malware has never been encountered before.
This ability to learn from subtle behavioral patterns significantly improves detection and response times to previously unseen threats, making deep learning essential in staying ahead of sophisticated cyberattacks.
Neural Networks
Neural networks are AI models inspired by the human brain’s structure. In them, nodes process data through weighted inputs. Each node evaluates its input, adjusting weights to improve accuracy. The final result is based on the sum of these evaluations. In cybersecurity, neural networks help analyze vast amounts of data, such as firewall logs, to identify patterns and predict potential threats, making them a powerful tool for threat detection.
Large Language Models (LLMs)
Large Language Models (LLMs), such as GPT-4, represent another significant AI technology in cybersecurity. LLMs specialize in processing and understanding human language, making them highly useful for automating threat analysis and improving security responses. These models can sift through vast amounts of text data—such as threat reports, logs, and documentation—to identify potential risks and patterns that could signal an attack.
LLMs also help with tasks like phishing detection, generating human-readable threat reports, and automating responses to security incidents. By understanding the context of language, they can enhance cybersecurity tools, enabling faster and more accurate decision-making.
Latest Developments in AI for Cybersecurity

1. AI-Powered Remediation
As AI continues to evolve, one of the most promising innovations is AI-powered remediation, which automates the response to security incidents in real-time. Traditional incident response processes often involve manual investigation, decision-making, and intervention, resulting in delays that give attackers more time to exploit vulnerabilities. AI-powered remediation, on the other hand, can immediately act on detected threats by isolating affected systems, blocking malicious traffic, or even rolling back compromised systems to a secure state.
2. Generative AI for Enhanced Threat Intelligence
Generative AI also creates more advanced threat intelligence tools, enabling real-time analysis of emerging threats and automatically generating security insights.
3. AI-Powered Security Automation
AI is now being leveraged to automate complex security processes, such as vendor questionnaires and incident response workflows, further improving the efficiency of cybersecurity teams.
4. Advanced Threat Deception Tactics
New developments in threat deception allow AI to create dynamic environments designed to mislead and trap cyber attackers, providing organizations with valuable intelligence while neutralizing threats.
How AI Powers Balbix
Balbix leverages advanced AI to revolutionize cybersecurity through continuous risk and exposure management. Its AI-powered platform automates threat detection, vulnerability prioritization, and security decision-making, helping organizations stay ahead of evolving threats. Balbix identifies and prioritizes risks based on business impact by analyzing vast amounts of data from various sources, enabling security teams to focus on the most critical issues.
Balbix’s machine learning algorithms continuously learn from new data, improving accuracy in identifying vulnerabilities, attack vectors, and potential breaches. This AI-driven approach ensures proactive risk reduction by automatically recommending remediation actions and optimizing workflows through intelligent automation.
Additionally, Balbix uses AI to quantify risk in financial terms, allowing businesses to align their cybersecurity strategy with broader financial goals. With its ability to detect, manage, and mitigate risks in real-time, Balbix’s AI enhances situational awareness, enabling organizations to make informed, data-driven security decisions and stay resilient in an increasingly complex threat landscape.
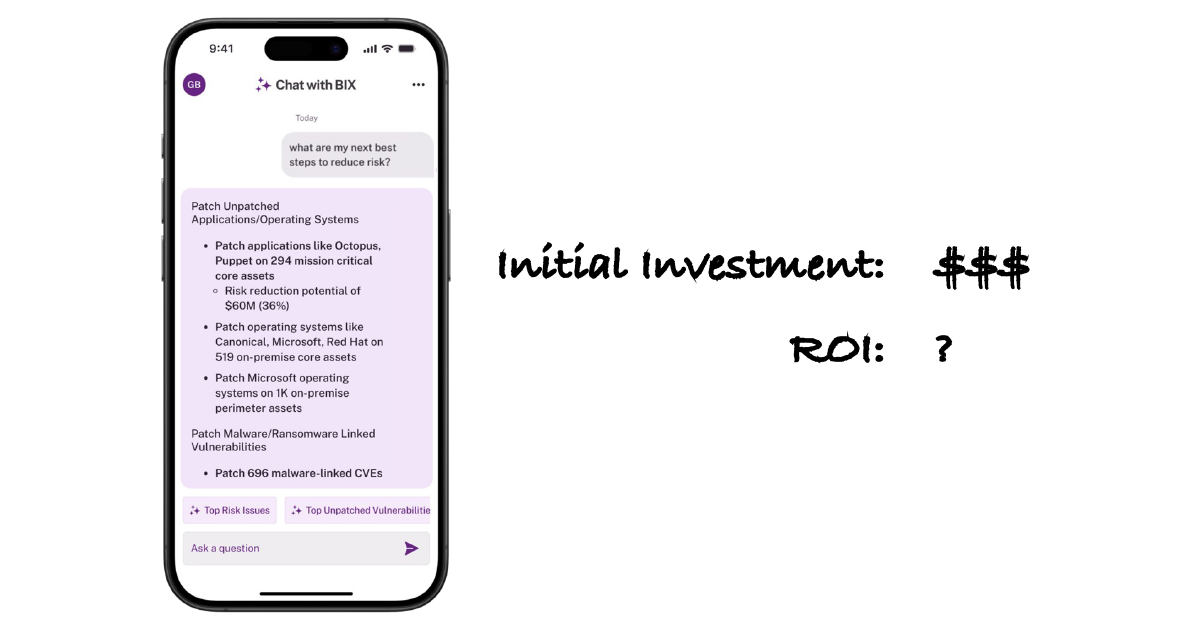
Lastly, Balbix offers BIX. BIX is an AI-powered cybersecurity assistant that provides personalized insights, recommendations, and risk-based guidance tailored to each user’s role and needs. It enhances decision-making with real-time context awareness, integrates with business systems, and offers a mobile-first experience to access critical information anytime, anywhere.
The Future of AI in Cybersecurity
As AI technology advances, its role in cybersecurity will continue to expand. Innovations such as quantum AI and more advanced language models hold the potential to enhance threat detection and response capabilities further.
However, cybercriminals are also adapting as AI becomes more prevalent in cybersecurity. We can expect AI to be used in more sophisticated cyberattacks, requiring organizations to stay vigilant and continuously update their defenses.
Frequently Asked Questions
- How can generative AI be used in cybersecurity?
-
Generative AI can significantly enhance cybersecurity by creating simulations and models to predict and counter cyberattacks. In cybersecurity, various AI types, such as machine learning, neural networks, and natural language processing, detect threats and automate responses. AI can also be utilized for cybercrime by analyzing vast amounts of data to identify vulnerabilities and generate phishing content, requiring ongoing efforts to safeguard against such misuse.
- What types of AI are used in cyber security?
-
In cybersecurity, various AI types shine brightly, acting as digital sentinels. These include machine learning, which helps predict and detect threats by learning from data patterns. Natural Language Processing (NLP) aids in analyzing and understanding cyber threats communicated through text. Lastly, deep learning, a subset of machine learning, identifies hidden threats by processing vast amounts of data. Together, they form a formidable defense against cyber adversaries.
- How can AI be used for cybercrime?
-
AI can automate hacking processes, making cyber attacks more frequent and sophisticated. It can also be used in phishing to create highly convincing fake messages.
Additionally, AI can analyze vast amounts of data to identify system vulnerabilities much faster than humans, to help better protect organizations from these AI attacks and more traditional attacks.